Install CloudDefense suite on a Kubernetes cluster
Pre-requisites
Install kafka
Install cdefense
Configure Social Authentication
Github
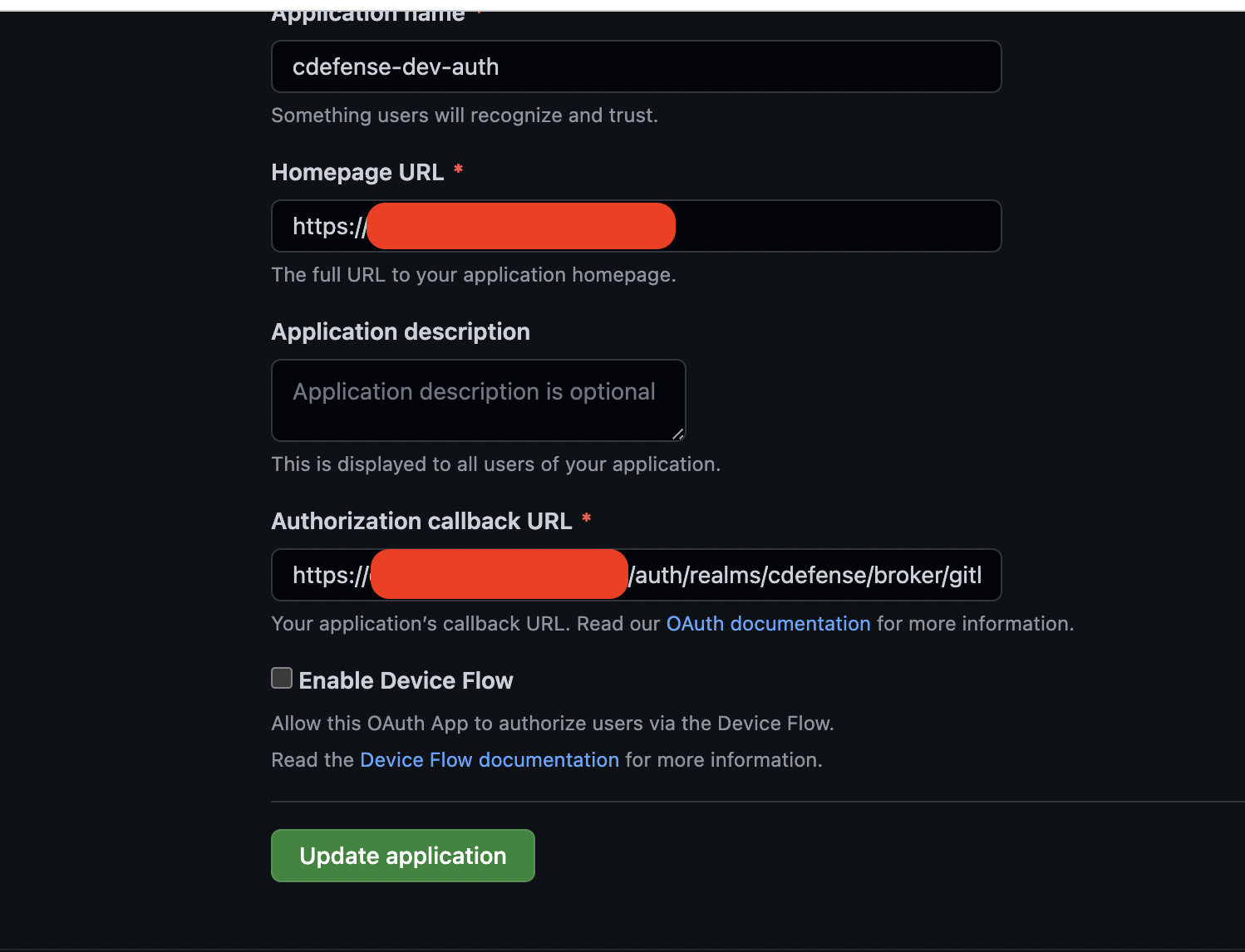
create secrets for authservice
How to change location of logs
in case of private bucket
Last updated